
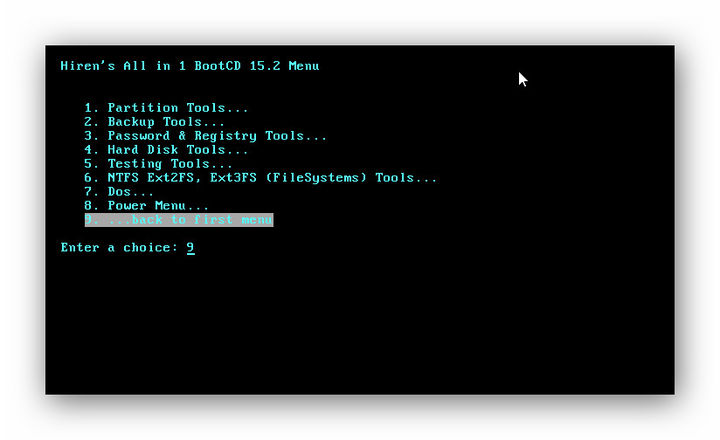
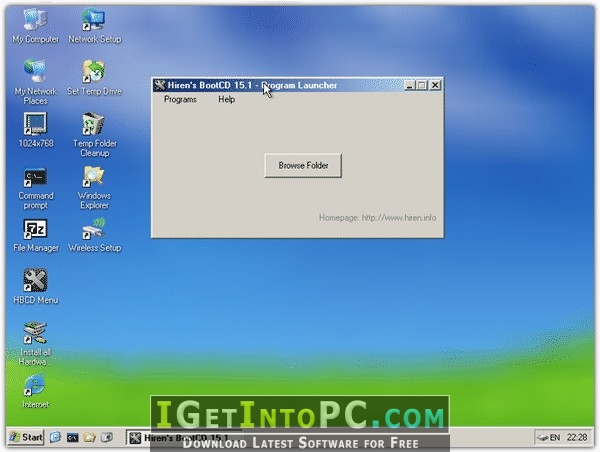
Hirens Boot CD 15.2 Tool to Fix & Repair All PC Problems. This kind of compilation software provides a compilation of programs to help resolves most and some uncommon Internet and computer issues like driver failure, intermittent internet connection and other computer malfunctions. Filename: HBCDPEx64.iso(Special thanks to our Supporters for maintaining fast and reliable mirror servers): Filesize: 1292.04 MB ( bytes) ISO MD5. HBCD Program Launcher 3.2: Hiren’s BootCD Program launcher (HBCDMenu.exe and HBCDMenu.csv) can be used to launch all these programs from USB/CD (Windows Freeware). Mouse Emulator 2.2: You can use your keyboard numpad as a mouse, very useful if your mouse broken or if you are having USB driver problems (Windows Freeware). It seems that Hiren’s Boot CD 15.2 version will be the last version of the author, because for a long time I have not seen the author have any movements. But earlier this year, this year 2018, the author of Hiren’s Boot released an upgraded version of his legendary computer rescue toolkit.
Changes From Version 15.1 to 15.2 New Added Softwares, Updated Functions: Updated Softwares: Troubleshoot If you are getting a virus warning from the downloaded files, please check FAQ page “Why am I getting a virus warning for a file downloaded from your website” section. If you are getting redirected to the download page or homepage while you are trying to download the file, please disable the softwares or settings can be blocking referer headers of your browser, connect directly if you are using a proxy, close your browser, clean browser cache and try again. Please check FAQ page for any other frequently asked questions. Filename: Hirens.BootCD.15.2.zipFilesize: 592.5 MB (621283886 bytes)ISO MD5: 7EFC81ADBBD551D56F6021C439C6837CZIP MD5: D342BBD6BF7554ABA24A376E41675DBF Antivirus Tools Backup Tools BIOS / CMOS Tools Award DMI Configuration Utility 2.43: DMI Configuration utility for modifying/viewing the MIDF contents (Dos Freeware).! Browsers / File Managers Cleaners Device Driver Tools OptimizersRelated: SecurityCryptoLocker Ransomware GPO Guide and FAQTable of Contents The purpose of this guide There is a lot of incorrect and dangerous information floating around about CryptoLocker. As BleepingComputer.com was one of the first support sites to try helping users who are infected with this infection, I thought it would be better to post all the known information about this infection in one place.
Hirens Boot Cd Version 15 26
TDSS. TDL-4We recently published an analysis of the TDSS rootkit, and just as we expected, TDSS continues to evolve. A new variant of the rootkit, TDL-4, which can infect both 32-bit and 64-bit operating systems, appeared sometime between July and August, 2010. In this article, we describe a new loading method used by the rootkit and examine how the rootkit bypasses PatchGuard and the Windows code integrity mechanism, the protection system built into 64-bit Windows operating systems. Components
Hiren's Boot Cd 16
Buckle Up key holder by ThabtoA Buckler of a Wall Key Holder! Get yourself fastened and get ready for a cute and pretty intelligent way of keeping your keys in order. This is the “Buckle Up” key holder for your rings and rings of keys which you’ve gotta hang up by the door or your bound to lose.crypto locker'What should you do when you discover your computer is infected with CryptoLocker When you discover that a computer is infected with CryptoLocker, the first thing you should do is disconnect it from your wireless or wired network. This will prevent it from further encrypting any files. Some people have reported that once the network connection is disconnected, it will display the CryptoLocker screen. It is not advised that you remove the infection from the %AppData% folder until you decide if you want to pay the ransom. If you do not need to pay the ransom, simply delete the Registry values and files and the program will not load anymore.
'nesting pc virtual tablet' by sono mocci - 'FUJITSU design award 2011' competition shortlisted entry'nesting pc virtual tablet' by sono mocci a concept by japanese-born, italy-based designer sono mocci , 'nesting pc virtual tablet' is a combination tablet and data visualization interface with automatic battery charging and data syncing. phones, memory cards, CDs, USB ports, and I/O cables can be plugged
Better Internal Vulnerability Scanning With AuthenticationIf you perform internal vulnerability scans, be sure that the scanning tool is configured to authenticate to the systems it is examining. Without this crucial step, your visibility into the systems’ security posture is drastically diminished. Here are a few considerations for defining the scanner’s login credentials. Unauthenticated Vulnerability ScansPlug Cup – Single Plugging Cup for Tea and Coffee by Dong Hun Seo, Geun Hyuk Yoo, Ki Sang Yoon & Yune Jae BangSingle Cup Special Oh boy, this Plug Cup is going to make me lazybones. Ever since I’ve laid my eyes on it, I have wanted this concept to come to life. It’s perfect for this instant coffee and green tea glutton that I am.
Security Bulletin MS14-011 - CriticalA remote code execution vulnerability exists in the way that the VBScript engine handles objects in memory. The vulnerability may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. To view this vulnerability as a standard entry in the Common Vulnerabilities and Exposures list, see CVE-2014-0271.
Hirens Boot Cd Free
Related: